In the world of technology, data, and innovation, presentations often lean heavily on facts, charts, and jargon. While these elements are crucial, they can sometimes overwhelm or bore an audience if presented without context. This is where storytelling becomes a powerful tool. By weaving narratives into technical presentations, speakers can simplify complex ideas, build stronger connections, and leave a lasting impression.
Storytelling in technical presentations isn’t about replacing data with drama. It’s about using narrative techniques to highlight the relevance of information and make it relatable to the audience. Whether you are presenting to investors, clients, or internal teams, stories provide structure and emotional impact that raw numbers simply cannot achieve.
Why Storytelling Matters in Technical Presentations
1. Simplifies Complex Concepts
Technical topics often involve layers of complexity—algorithms, coding languages, system architectures, or intricate workflows. For many audiences, understanding these details can feel overwhelming. Storytelling bridges this gap by translating complexity into relatable terms.
For instance, instead of diving directly into the technicalities of cybersecurity encryption, you might start with a story about how digital “locks and keys” protect valuables in the online world, much like a safe in a house. This approach helps non-technical stakeholders quickly grasp the concept before you expand into the technical details.
2. Engages Audience Emotionally
Facts appeal to logic, but stories appeal to emotion—and emotion drives memory and decision-making. A well-structured story can capture your audience’s attention and make them feel invested in the outcome.
For example, when presenting a healthcare AI solution, instead of starting with accuracy percentages, you could share a story of a patient whose life was improved by early diagnosis. This emotional entry point creates empathy, which makes the audience more receptive to your data and technical explanations.
3. Provides Structure and Flow
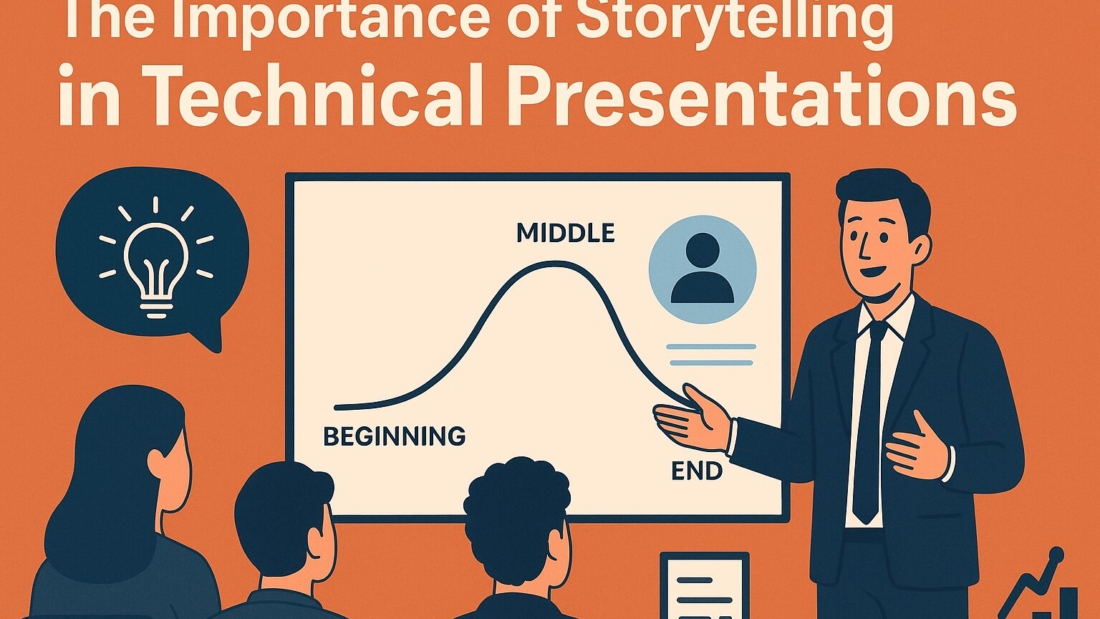
Stories naturally have a beginning, middle, and end. Applying this structure to technical presentations ensures your message doesn’t get lost in scattered details. By framing your content around a narrative arc—problem, solution, and outcome—you provide a clear path for the audience to follow.
This approach not only keeps the audience engaged but also helps you, as the presenter, stay organized and avoid overwhelming listeners with too much data at once.
4. Makes Content Memorable
Numbers fade quickly from memory, but stories stick. Research shows that people are more likely to recall information embedded within a narrative compared to standalone facts. When your technical presentation includes stories, your audience is more likely to remember key takeaways long after the meeting ends.
Think about how often people recall a customer success story versus remembering exact technical specifications. The story provides a mental anchor that reinforces the technical details.
5. Enhances Persuasion
Technical presentations are often designed to persuade—whether it’s to secure funding, win a client, or convince leadership to adopt a new system. Stories strengthen persuasion by demonstrating real-world impact.
For instance, presenting a case study in the form of a story about how your solution solved a major business challenge is more persuasive than simply showing before-and-after charts. It adds credibility and paints a vivid picture of success.
Practical Tips for Using Storytelling in Technical Presentations
While the benefits are clear, the real challenge lies in implementing storytelling effectively. Here are some actionable strategies:
Know Your Audience
Before crafting your story, consider who will be in the room. Are they technical experts, business executives, or end-users? Tailoring your story to their level of knowledge and interests ensures maximum engagement.
Start with a Hook
Open with a relatable scenario, question, or anecdote that draws your audience in. For example: “Imagine waking up one morning to find your company’s entire customer database exposed online…” Such an opening immediately captures attention before you dive into technical explanations.
Use Analogies and Metaphors
Analogies make complex concepts easier to grasp. For instance, explaining cloud computing as a “virtual warehouse” is more relatable than discussing server configurations in isolation.
Integrate Data into Stories
Numbers and statistics are essential in technical presentations, but embedding them in stories makes them more compelling. Instead of saying “our system reduced downtime by 25%,” frame it as: “Before adopting our system, a downtime incident meant hours of halted operations. Now, thanks to our solution, that downtime has been cut by 25%, saving thousands in lost productivity each month.”
Keep It Authentic
Stories should feel real and authentic. Overly polished or exaggerated narratives can reduce credibility. Use real-world case studies, personal experiences, or customer testimonials whenever possible.
Common Pitfalls to Avoid
While storytelling is powerful, it can backfire if misused. Here are some pitfalls to watch out for:
Overcomplicating the Story: If your narrative is too long or detailed, it can overshadow the technical content. Keep it concise.
Ignoring Data: Stories should complement data, not replace it. A strong presentation balances both.
Using Irrelevant Stories: Every story must support your key message. Irrelevant anecdotes can confuse or disengage the audience.
Conclusion
In technical presentations, storytelling is not a luxury—it’s a necessity. It helps simplify complex ideas, engages audiences emotionally, provides structure, improves memorability, and strengthens persuasion. By integrating stories into your technical presentations, you can transform dry data into compelling narratives that resonate long after the slides are over.
Whether you’re addressing investors, clients, or colleagues, remember that people don’t just buy into numbers—they buy into stories. In today’s fast-paced and information-heavy world, storytelling is the bridge that connects your technical expertise with meaningful impact.